Technical Deep Dive
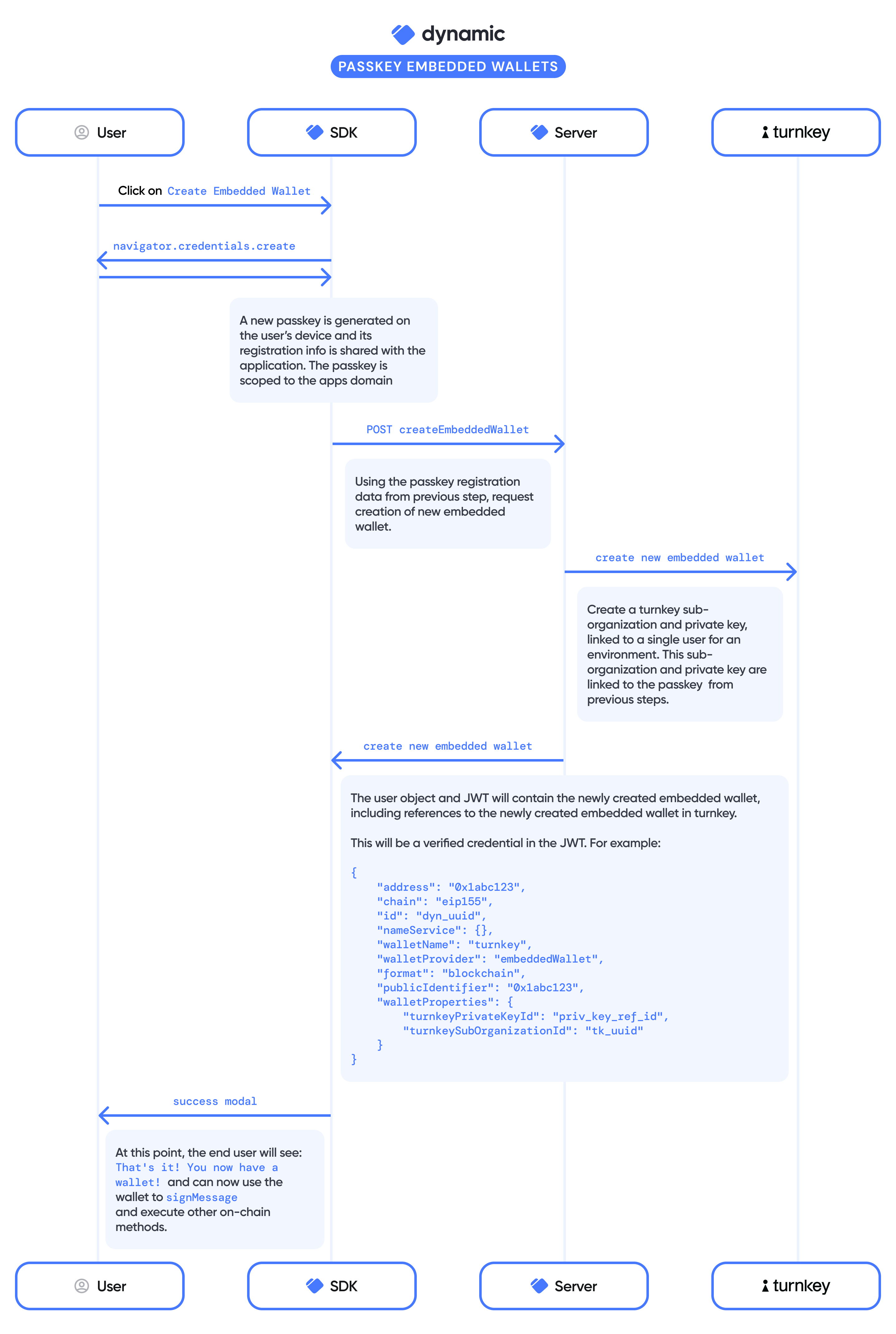
You have installed the Dynamic SDK, chosen your end-user auth method, and enabled embedded wallets. The End User comes to your website and initiates account creation, what actually happens now?- Dynamic authenticates the End User via Email OTP or Social Sign-in.
- After authentication, the user is prompted to create a passkey, which leads to embedded wallet creation.
- The user’s device requests a biometric. A passkey is generated.
- Dynamic sends a Challenge (a random sequence of numbers of letters), which is automatically signed, forming a signature to confirm user control. The user’s credential is safeguarded in their device’s enclave.
- Post-signature, Dynamic instructs, our non custodial key management provider to create a wallet.
- Turnkey checks passkey details and links them with the user, an action encrypted in an AWS Nitro Enclave. Dynamic receives a UUID to associated the key with its user.
- With a confirmed wallet, users can secure transactions using the passkey.
Important notes
Domains
Domains
Passkeys are scoped to top level domains - This means that they will work on
app.example.com, example.com, and market.example.com, but will require a new passkey if interacting on on
app.example.xyz or notexample.com. If a customer interacts with your application on a different domain, the user’s account and wallet will appear as expected. Dynamic will detect that they are attempting to interact with a wallet on a new domain and prompt them to add a new passkey or use a one-time (if enabled) to complete the transaction.If you decide to migrate your domain, your
end users will need to generate new passkeys. We can walk you through that
process as you implement.
Exporting
Exporting
You can utilize our export feature to export both recovery phrase and private key.
Browsers
Browsers
Passkeys are supported on the following browsers:Android: Chrome, BraveMacOS v13+ Safari, Chrome, BraveiOs v16+: Safari, Chrome, BraveWindows: Chrome, EdgeNot Supported:Chromebook: Not supportedOpera MiniFor customers that are on an unsupported browser, we recommend they update to the a recent version
1Password
1Password
(Requirement: 1password installed on both desktop and phone)Delayed syncing across mobile: Passkey may not sync to the mobile device when it is created first on desktop. User may have to adjust their 1pass password settings in IOS to allow 1password to auto-fill browsers.
Not pairing: Even if the 1password is installed on both devices, iOS sometimes does not check 1password for passkeys. This prevents a user from accessing their passkey on their mobile device. To remediate, open password options under settings on your iOS device. Make sure that 1Password is selected to auto-fill for passwords and passkeys. If its already selected, deselect and re-enable in order to refresh it.
Multi-Chain
Multi-Chain
Passkeys are assigned at wallet creation, meaning the same passkey can be used for all embedded wallets created at the time of passkey creation. Adding additional embedded wallet chains will require users to use their passkey. Support for adding an embedded wallet on a new chain for existing embedded wallet users will be availalbe in the coming weeks.
FAQ
What are passkeys?
What are passkeys?
Passkeys are a new type of passwordless authentication designed to be more
secure and convenient than traditional passwords. They are based on the Web
Authentication (WebAuthn) standard, which uses public key cryptography to
create a secure link between a user’s device and a website or app. They were
developed by the FIDO alliance (made up of companies like Apple, Google,
Microsoft, Amazon, 1Password, among others).Unlike traditional passwords,
which create friction and pose phishing risks, passkeys leverage a familiar
pattern of using a biometric (FaceID, or TouchID) to securely create and store
a credential to the user’s device.
How is Dynamic using passkeys?
How is Dynamic using passkeys?
Dynamic uses passkeys as a security method to authenticate and gate access to
embedded wallet private keys. Specifically, passkeys are used to ensure that
your users are in control of their private keys by leveraging secure enclaves.
By simple analogy, passkeys and secure enclaves are similar to a safety
deposit box vault. That is, your end users have a key to access their locked
box (i.e., wallet), while enjoying the benefits of having the box secured with
vault-level security. The safety deposit box is inside the vault, but only the
end user, with their key, can access the contents inside the box. After
authenticating via email or social, users are prompted to create a passkey
with their device (e.g., biometrics). This grants them a wallet and enables
transaction signing with that passkey. The wallet’s private key is encrypted
at rest, and only decrypted within secure enclaves with a signature from the
user’s passkey.
How do passkeys protect against sim swapping and phishing attempts?
How do passkeys protect against sim swapping and phishing attempts?
Passkeys come with multiple built in security benefits. Specifically, unlike a
password or passcode, a user doesn’t have to remember information with a
passkey, and that information can’t be phished from the user. In addition,
because passkeys are tied to your iCloud or Google accounts, they are
protected by Apple and Google’s security. Even if your sim gets swapped, an
attacker would farther have to gain access to your iCloud account or Google
keychain in order to get access to your passkey